Double Strength Encryption
Double strength encryption, also called as multiple encryption, is the process of encrypting an already encrypted text one or more times, either with the same or different algorithm/pattern.
The other names for double strength encryption include cascade encryption or cascade ciphering.
Levels of Double Strength Encryption
Double strength encryption includes various levels of encryption that are explained here under −
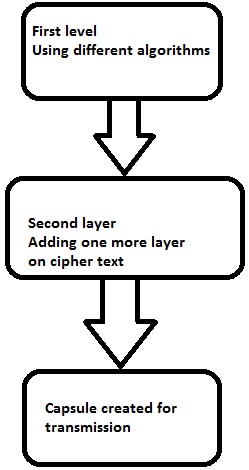
First layer of encryption
The cipher text is generated from the original readable message using hash algorithms and symmetric keys. Later symmetric keys are encrypted with the help of asymmetric keys. The best illustration for this pattern is combining the hash digest of the cipher text into a capsule. The receiver will compute the digest first and later decrypt the text in order to verify that text is not tampered in between.
Second layer of encryption
Second layer of encryption is the process of adding one more layer to cipher text with same or different algorithm. Usually, a 32-bit character long symmetric password is used for the same.
Third layer of encryption
In this process, the encrypted capsule is transmitted via SSL/TLS connection to the communication partner.
The following diagram shows double encryption process pictorially −
Hybrid Cryptography
Hybrid cryptography is the process of using multiple ciphers of different types together by including benefits of each of the cipher. There is one common approach which is usually followed to generate a random secret key for a symmetric cipher and then encrypt this key via asymmetric key cryptography.
Due to this pattern, the original message itself is encrypted using the symmetric cipher and then using secret key. The receiver after receiving the message decrypts the message using secret key first, using his/her own private key and then uses the specified key to decrypt the message.
